Network security technologies protect IT systems, platforms, and applications from many internet attacks through prevention and automatic response. These are now essential deployments in the fight against cybercrime.
The increasing dependence on IT infrastructure was shown by the number of companies that struggled to cope when the COVID-19 pandemic struck. It was striking how many large organizations’ had not prepared their networks for such large numbers of employees working from home even though their disaster-recovery plans should have covered such an unlikely eventuality.
However, as Gartner Group has pointed out, hybrid IT architectures that include both on-premise and cloud are becoming more widely adopted: “Organizations must set a strategy that will become our “new normal” in these uncharted waters. It remains true that no single security technology provides a complete prevention solution, and organizations still require a defense-in-depth approach. Therefore, a key requirement for setting an organizational network security strategy is to understand the available controls in the marketplace and ascertain if they remain relevant in hybrid and multi-cloud infrastructures. Security and risk management leaders are not able to prepare for every scenario. Therefore, they must make intelligent, risk-based decisions about which security technologies they may choose to defend their organization from threats and to maintain their day-to-day operations.
Meanwhile, attackers are becoming far more sophisticated. More than ever, the need for preventive security technologies that are agile and compatible with a broad spectrum of enterprises’ IT infrastructure models is paramount. Given the threat these attackers pose to every organization, prevention must be high on the corporate agenda.
No single security technology provides a complete solution, and organizations need to employ multiple systems to cover every possible attack vector. A security strategy must understand the available systems in the marketplace and determine if they remain relevant in hybrid and multi-cloud infrastructures.
The Gartner Hype Cycle for Network Security 2020
The Gartner Hype Cycle contains details on a representative section of technologies used by security leaders in organizations to mitigate and prevent threats, reducing risk to their infrastructures.
This is a fascinating Hype Cycle as 6WIND, which has over 15 years of experience in this field, is well-placed to boost companies’ performance in the key technologies outlined in the Hype Cycle and dealt with in this blog.
Figure 1
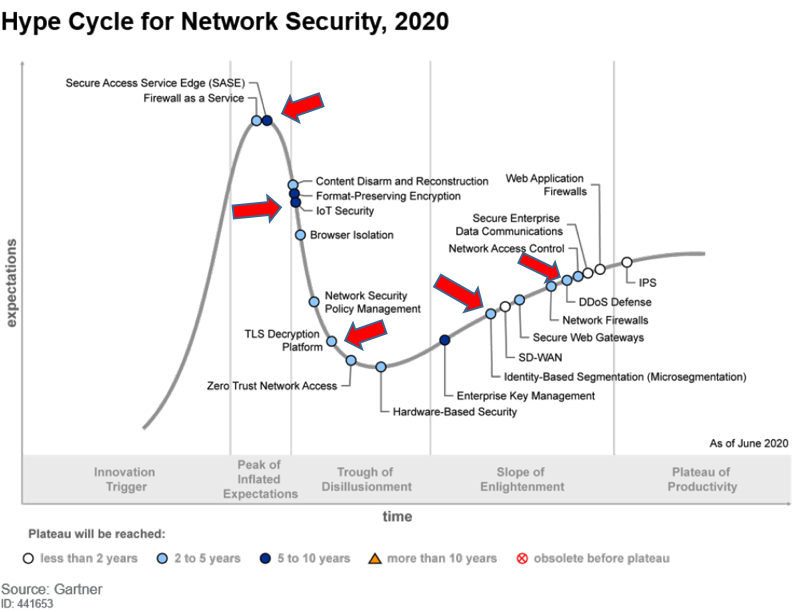
The red arrows indicate areas where 6WIND’s solutions can benefit your organization. As you can see, 6WIND technology covers the main areas and pathways of The Hype Cycle. To see our full range of solutions please visit https://www.6wind.com
Highlighted below are the Hype Cycle technologies that 6WIND can add value to at the networking level:
Secure Access Service Edge (SASE)
SASE delivers multiple capabilities such as SD-WAN, Secure Web Gateways (SWG), Cloud access security broker (CASB), next-generation firewall (NGFW), and zero-trust network access (ZTNA). SASE supports branch office and remote worker access and is delivered as a service and based on the device/entity’s identity, combined with real-time context and security/compliance policies. Identities can be associated with people, devices, the internet of things (IoT), or edge computing locations. As the network reaches further out to the edge, IoT, and identity management loom as considerable threats to the unprepared company.
Proper SASE services are cloud-native – dynamically scalable, globally accessible, typically microservices-based, and multitenant. The breadth of services required to fulfill the broad use cases means very few vendors will offer a complete solution in 2021.
With 6WIND’s core technology, the source code Foundation for next-generation networking applications, we enable OEMs to build high performance, scalable, and secure networking products for 5G, SD-WAN, IoT markets, and more
The Internet of Things
Internet of Things (IoT) security addresses software, hardware, network and data protection for digital initiatives involving IoT.
Gartner says: “SASE will enable I&O and security teams to deliver the rich set of secure networking and security services in a consistent and integrated manner to support the needs of digital business transformation, edge computing and workforce mobility. This will enable new digital business use cases (such as digital ecosystem and mobile workforce enablement) with increased ease of use while at the same time reducing costs and complexity via vendor consolidation and dedicated circuit offload.
“Some buyers will implement a well-integrated dual vendor best-of-breed strategy while others will select a single vendor approach. Expect resistance from team members that are wedded to appliance-based deployments.”
6WIND vRouter solutions leverage the 6WIND’s core technology to help realize, quickly and efficiently, the benefits of 5G, IoT, and SD-WAN.
TLS decryption platforms
Gartner emphasizes the importance and complexity of building a decryption strategy: “Enterprises slow to adopt web traffic SSL decryption best practices risk exposing their infrastructure to targeted malware campaigns and data loss.
“Evolutions of ransomware that leverage encryption for malware delivery and command-and-control communications will have higher financial costs because of the typically longer times before they are detected within an organization’s network.”
According to zscaler: “Many people assume that encrypted traffic means safe traffic. But that false sense of security creates risk because it means that the majority of organizations allow encrypted traffic to go uninspected, and attackers know this. The problem is that most security teams can’t fully inspect SSL traffic, as their legacy tools lack the processing power to decrypt, inspect, and re-encrypt packets without bringing performance to a standstill.”
However, 6WIND technology allows efficient usage of TLS. 6WIND provides TLS based high-performance solutions to build efficient TLS decryption platforms capable of mitigating the evolutions of ransomware that leverage encryption for malware delivery.
SD-Wan
Software-defined wide-area network (SD-WAN) products replace traditional branch routers. They provide several features: dynamic path selection, based on business or application policy; centralized policy and management of WAN edge devices, and zero-touch configuration.
6WIND provides different solutions with enhanced performance and security to help its customer realize the benefits of SD-WAN and improve the cost and performance of their enterprise WANs.
Many companies host their services on different cloud platforms such as Amazon Web Services, Microsoft Azure, Google Cloud Platform, and more.
As these services are critical for access to their cloud, Service Providers cannot rely on Internet connectivity. Companies require a direct connection to their Cloud Service Providers for high bandwidth, reduced latency, and improved stability. Multi-cloud Service Providers exist to connect these different cloud services and provide an all-in-one peering solution. Customers are provisioned with filtering rules and routing tables, with allocation of specified bandwidth capacity.
6WIND’s vRouter gives Service Providers a software alternative to hardware routers for multi-cloud routing use cases.
Secure Web Gateways
Secure web gateways (SWG) protect users from web-based threats and enforce corporate web-usage policies. Users do not connect directly to websites, instead, they access the SWG, which in turn connects them to the website while also carrying out URL filtering, web visibility, malicious content inspection, web access controls, and a number of other security checks such as protecting data against unauthorized transfer.
As enterprise mobile workforces grow, it becomes increasingly difficult to protect them from threats. This is because organizations typically have a variety of applications, some at their headquarters and others in the cloud.
Applications at a company’s headquarters are usually accessed via a remote access Virtual Private Network (VPN). However, when users access cloud applications, they are disconnected from the VPN – exposing them to considerable risk. SWGs are used to provide secure internet access when users are disconnected from the VPN.
Given the critical role employees play in IT security, web gateways are one of the top IT security spending priorities.
The popularity of web gateways won’t be waning anytime soon. Analysts generally expect 20% growth in the web gateway market for the foreseeable future, with sales more than doubling to $12 billion by 2025.
6wind IP Security (IPsec) Virtual Private Network (VPN) solutions are critical networking infrastructure used to create secure, high-speed communication tunnels between trusted endpoints across the Internet. Examples include site-to-site VPNs for secure connectivity between data centers and between remote sites for corporate networks. 6WIND can provide SSL proxy solutions based on 6WINDGate to mitigate the requirements and challenges organizations face.
Network Firewalls
Network firewalls filter internet transmissions to ensure that only authentic traffic is allowed into an organization. Decisions are made by network administrators on pre-set rules or policies. A network firewall analyzes traffic to decide if the packets can enter based on source, destination, protocols, and ports. Until recently this was done with static filtering that inspected only packet headers. However, hackers figured out that all they had to do was change the packet header information to something expected and they were allowed into the network. As a result, dynamic packet inspection was created. Outgoing packets are examined for a specific type of incoming packet. Only the ones with the proper correspondence are allowed to pass. Some types of firewall protection can also provide UTM functions with outgoing traffic to prevent command and control (C&C) traffic.
With 6WIND’s high-performance data plane, 6WINDGate can provide reliable solutions to fulfill the network firewall challenges.
Conclusion
Global spending on security hardware, software, and services topped $103 billion in 2019, up 9.4 percent from 2018, with large enterprises spending the most, according to IDC. IDC projects that global spending on security is growing at a compound annual growth rate of 9.2 percent. In 2022, IDC forecasts security-related expenditure will be $133.8 billion. Large companies with 500 to more than 1,000 employees will account for two-thirds of security spending. The U.S. will spend the most on security with manufacturing and federal government accounting for 20 percent of the total.
According to The European Union Agency for Cybersecurity we can expect significant changes in the way we perceive and understand cybersecurity or the security of cyberspace. In its recent Emerging Trends report the agency says: “The protection of individuals, business and organizations while using cyberspace will tend to shift during the next decade, from the traditional network and information security (NIS) to a wider concept including content and services. Because of the current COVID-19 pandemic, we initiate the decade with a new norm and profound changes in the physical world and cyberspace. With social distancing or confinement, people will tend to use the virtual space to communicate, relate and socialize. This new norm will introduce new challenges across the digital value-chain and in particular, the cybersecurity industry. During the next decade, cybersecurity risks will become harder to assess and interpret due to the growing complexity of the threat landscape, adversarial ecosystem, and expansion of the attack surface.”
The future of network safety is in the Cloud – but the real secret to keeping safe is to start preparing now!
See Figure 2 (below) for more detail.
Figure 2

Table of Contents


![10.16.1oo.244 FTP Server Guide [Updated 2024] 10.16.1oo.244](https://www.techiemag.net/wp-content/uploads/2021/09/10.16.1oo.244-238x178.png)
![Modern app LTD app [Updated 2023] Modern app LTD app 2021](https://www.techiemag.net/wp-content/uploads/2021/08/shutterstock_copd1-1168x657-1-238x178.jpg)
![172.16.50.4 Movie Server IP Address [2023] 172.16.50.4 / 172.16.50.04 / 172.16.50.o4](https://www.techiemag.net/wp-content/uploads/2021/09/172.16.50.4-techiemag-238x178.png)
![[Jan 2024] EZTV Proxy | Unblock EZTV | EZTV Alternatives eztv](https://www.techiemag.net/wp-content/uploads/2020/05/eztv-300x194.png)
![TikTok Download PC [2021] TikTok Download PC [2021]](https://www.techiemag.net/wp-content/uploads/2021/09/tiktokgames1-1582147342563-100x75.jpg)

